The landscape of server threats is rapidly evolving as cybercriminals become increasingly sophisticated. The cost of these attacks is mounting, impacting organizations and governments alike. For instance, in April 2022, the ransomware group Conti executed extensive attacks on the Costa Rican government, disrupting nearly 30 ministries and essential services. This breach prompted the President of Costa Rica to declare a state of National Emergency—a first for a cyberattack. Similarly, Shields Health Care Group experienced a breach affecting nearly 2 million patient records, while Medibank Private Ltd., a major Australian health insurer, had data on 9.7 million customers stolen, with threats of publishing this information unless a ransom was paid.
Given that servers form the backbone of modern businesses, handling vast amounts of sensitive data, securing them is imperative. The stakes include financial losses, reputational damage, and legal ramifications. To combat these threats, Microsoft introduced Secured-core servers in 2021, collaborating with silicon partners and original equipment manufacturers (OEMs) to offer advanced hardware-based security. In this post, we’ll explore how Windows Server 2025’s Secured-core servers integrate seamlessly with Microsoft’s broader security ecosystem to identify and thwart real-world attacks.
Understanding the “Bring Your Own Vulnerable Driver” (BYOVD) Attack Technique
A notable attack technique, known as “Bring Your Own Vulnerable Driver” (BYOVD), involves adversaries exploiting a legitimate but vulnerable driver installed on a target system. This technique grants attackers high-level system privileges, enabling them to disable security processes. Two examples of such drivers are:
- kprocesshacker.sys: Used by the DoppelPaymer ransomware, which targeted companies like Foxconn and Kia. DoppelPaymer hijacks Process Hacker, a malware analysis tool, to terminate security processes by dropping malicious drivers and DLLs into a subdirectory of
%APPDATA%. - asWarPot.sys: Utilized by the AvosLocker ransomware, targeting critical infrastructure sectors. This driver, a legitimate but vulnerable Avast Anti-Rootkit driver, was exploited to disable endpoint protection on targeted systems.
How Secured-core Servers and Microsoft Defender for Cloud Defend Against Modern Threats
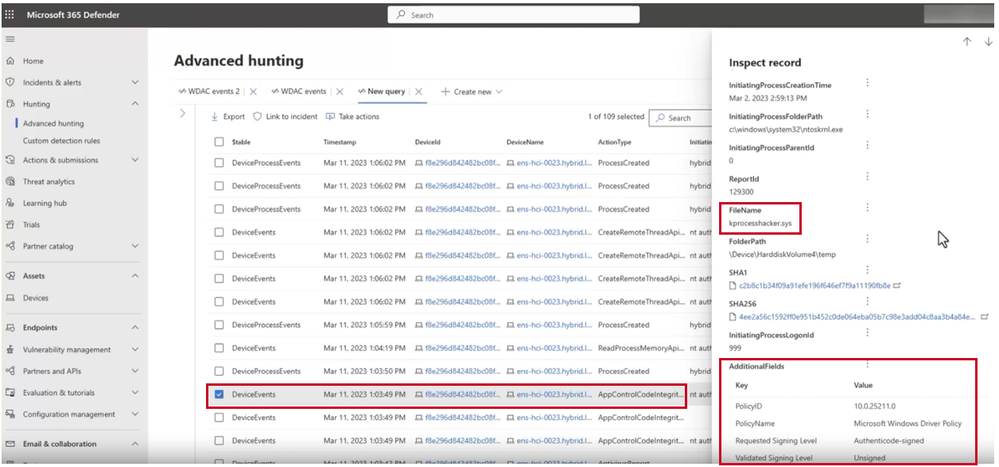
Defense Against kprocesshacker.sys
Secured-core servers feature Hypervisor-protected Code Integrity (HVCI), leveraging Virtualization-based Security (VBS) to run kernel mode code integrity in a secure environment. HVCI’s code integrity policy maintains a blocklist of vulnerable drivers, preventing the loading of malicious drivers like kprocesshacker.sys. Event logs in Windows Admin Center provide insights into blocked drivers, demonstrating how Secured-core servers proactively protect against such threats.
Defense Against asWarPot.sys
Microsoft Defender for Cloud continuously monitors for threats across your servers. When a vulnerable driver like asWarPot.sys is detected, Defender for Cloud blocks the malicious action and alerts IT administrators based on configured preferences. This real-time monitoring helps identify suspicious activities and threats, with Defender for Endpoint agents installed on servers providing detailed insights into attack chains, facilitating a thorough understanding of the events leading to a threat.
Enhancing Security with Secured-core Servers
Secured-core servers provide a robust foundation for server security, integrating with Microsoft’s security suite to offer enhanced threat detection, alerting, and remediation. The adoption of Secured-core servers has been growing steadily since their introduction. By 2022, Secured-core became a prerequisite for all new Azure Stack HCI solutions based on Gen 3 or newer server-grade silicon platforms. Major manufacturers like Dell Technologies, HPE, and Lenovo now support Secured-core servers across their products.
To explore the latest Secured-core servers and solutions, visit the Windows Server catalog or the Azure Stack HCI catalog.